Coming soon
Coming soon
Coming soon
News & Events
HoliDex
Contests
Academy
NFTs Marketplace
Testimonials
Promotion
Management links
All Services











OTHER
ALL SERVICES
Language


Crypto Security: How to Protect Yourself from Scammers
- Tips for Crypto Security
- A stranger contacts you with an offer to earn money or help
- You are added to a project chat or channel
- Any website can be faked
- A friend contacts you with a suspicious offer or request
- Your wallet is asked to connect to something
- A "project admin" reaches out offering assistance
- You are offered to buy tokens at a special price or directly
- Tokens appear in your wallet that you didn’t purchase
- A new wallet appears on a marketplace
- Fake startups
- Scams involving crypto purchases through P2P exchanges
In today's world, scammers are becoming increasingly inventive, devising schemes that can deceive even the most experienced users. These actions aim to gain access to others' funds or data, making it crucial to understand how to identify such threats.
Tips for Crypto Security
To reduce the risks of wallet hacks or loss of funds, follow these guidelines:
1. Verify Website URLs
Ensure you are using the official exchange website to avoid phishing attacks.
2. Use Two-Factor Authentication (2FA)
Always enable 2FA for account access to minimize the risk of unauthorized logins.
3. Store Large Amounts in Personal Wallets
Exchanges, especially centralized ones, are not meant for long-term storage of assets. Use hardware or cold wallets instead.
4. Choose Platforms with Transparent Reputations
For instance, HoliDEX leverages blockchain technology and verified smart contracts to help minimize risks for users.
5. Never Share Private Keys
Do not share your private keys or seed phrases, even if requested by someone claiming to be support.
6. Use Strong and Unique Passwords
Avoid reusing passwords across different exchanges or services.
7. Check Fees
Before making a transaction, ensure that conditions are transparent to avoid unexpected costs.
8. Review Smart Contracts
When using decentralized exchanges, stick to platforms with audited and verified code.
9. Keep Software Updated
Regularly update exchange apps, wallets, and browsers to patch vulnerabilities.
10. Be Cautious with Public Wi-Fi
Avoid accessing exchanges through public networks to prevent data interception.
Now, let’s explore some of the most common scams.
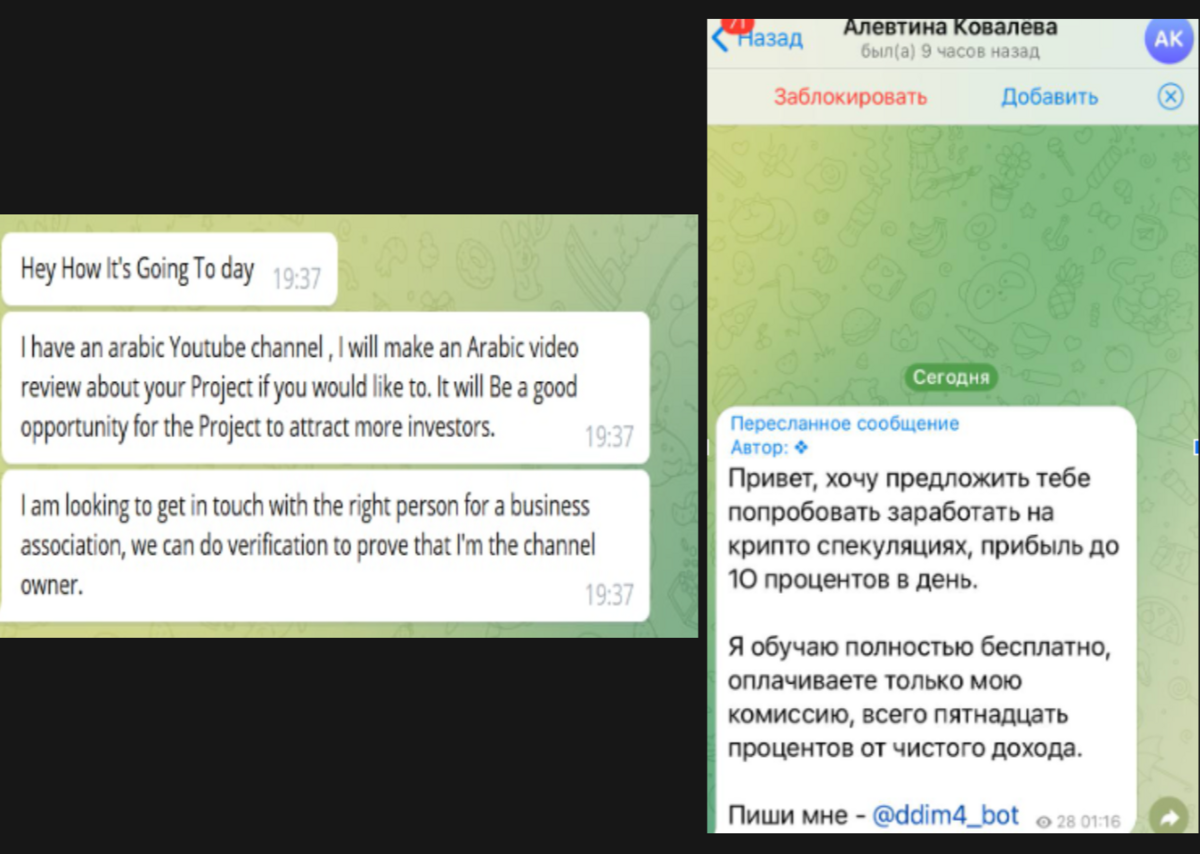
A Stranger Contacts You with an Offer to Earn Money or Help
Scammers often pose as well-known individuals, such as project leaders, to gain your trust. However, remember that such people rarely contact users directly. Always verify the sender's profile and pay attention to details like the username and account information. Never respond to these messages, click on links, or engage with the provided contacts. Promises of easy money or quick profits are usually traps to steal your data or funds. Ignoring such messages is the best protection.
You Were Added to a Project Chat or Channel
In the crypto world, staying informed, exploring opinions, and analyzing data is essential, making chats and channels valuable tools for users. However, scammers exploit this by creating fake channels and chats disguised as promising projects, exclusive VIP groups, or information hubs. Users are often mass-added to these chats or sent invitations, making it harder to identify fraudulent groups among genuine subscriptions.
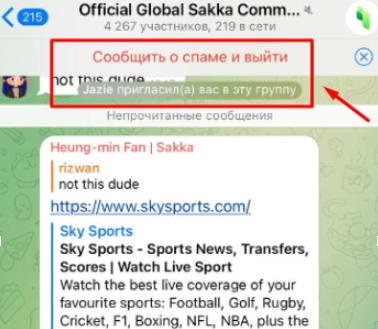
These channels often look professional, offering promises of exclusive opportunities, recommendations, or investment signals. To avoid being scammed, only subscribe to chats you have personally found and added yourself. For added security in Telegram, disable the auto-add to groups feature.
If you voluntarily join a chat, scammers may begin messaging or calling you, posing as support representatives to gain access to your funds. Stay vigilant and avoid sharing any sensitive information.
If you voluntarily join a chat, scammers may begin messaging or calling you, posing as support representatives to gain access to your funds. Stay vigilant and avoid sharing any sensitive information.
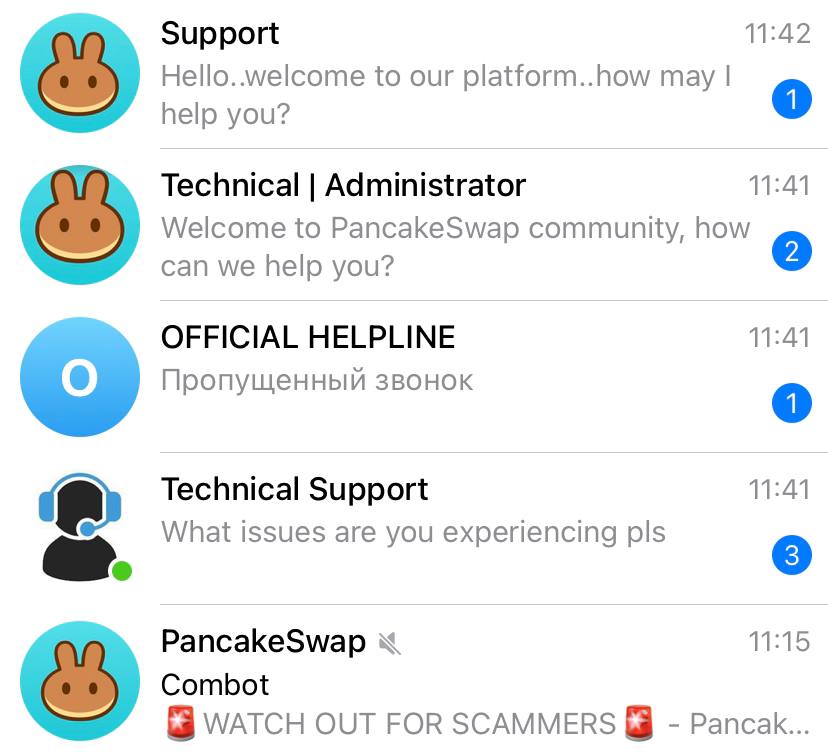
Any Website Can Be Faked
New users often search for service websites through standard search engines, which can lead them to phishing sites designed to steal funds. Scammers create fake websites that look identical to the original to deceive users.
How to Protect Yourself:
How to Protect Yourself:
- Check the URL: Ensure the website address matches the official one. For example, the official site for the Holiverse project is holiverse.ai.
- Use Bookmarks: Save verified websites in your browser bookmarks and access them directly.
- Be Cautious with Ads: Phishing sites can appear in search engine ad spaces. Prioritize organic search results over ads.
- Verify the Security Certificate: Look for a lock icon in the address bar and the "https://" prefix, which indicate a secure connection.
A Friend Contacts You with a Suspicious Offer or Request
If you receive a message from a friend with an unexpected request or offer—such as making easy money, buying tokens through a third party, or transferring funds—be cautious. It’s likely a scam. Call the person directly to confirm whether they actually sent the message.
Scammers often impersonate accounts by copying photos, descriptions, and usernames, making them almost indistinguishable from the real ones. They frequently pretend to be well-known figures, such as company CEOs or project staff.
To verify the authenticity of a message, cross-check the information with other company representatives, such as moderators or colleagues you’ve previously interacted with. Never rush to act on such requests without confirming the account’s legitimacy.
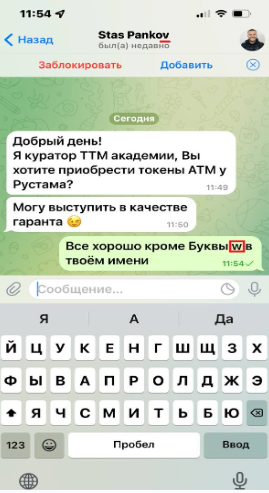
Your Wallet Is Asked to Connect to Something
Scammers often pose as project support, creating a professional appearance to gain trust. They may offer to "check an issue" via a site that looks official but is actually fake. These sites typically have a "Connect Wallet" button or ask for your seed phrase. Falling for these requests can lead to the complete loss of your funds.
Never connect your wallet to unverified sites or enter your seed phrase. For testing, use a separate wallet with a minimal balance and always verify the platform's authenticity.
A "Project Admin" Contacts You Offering Help
Scammers often impersonate administrators or CEOs of projects to gain trust and steal funds. The scenario is similar to other schemes: they reach out first, offer assistance, ask questions, and eventually lead you to actions that put your assets at risk.
Remember, administrators of legitimate projects never initiate contact with users. If you receive such a message, do not respond, and verify the information through official channels.
You Are Offered to Buy Tokens at a Special Price or Directly
Scammers exploit users' interest in new projects and token presales to steal funds. They may add you to "exclusive sale" chats, congratulate you for being on a whitelist, or claim that the token is already listed. These messages often include links to fake sites or exchanges where scammers create counterfeit tokens with similar names. Users are rushed to act, creating a false sense of exclusivity, leading to impulsive decisions.
To protect yourself, always verify the token contract address through official project sources. On platforms like HoliDEX, the decentralized structure ensures transparency and security for operations, allowing you to check tokens before transacting. Never send funds without confirming the authenticity of the token—this will safeguard you from asset loss.
Tokens You Didn't Purchase Appear in Your Wallet
The "Honey Pot" scheme involves scammers sending tokens to your address, creating the illusion of value. These tokens may have artificially inflated prices to attract attention. However, attempting to sell or exchange them often results in blocked sales, excessive fees, or other restrictions due to malicious code embedded in the token's contract.
This scheme also exploits the popularity of airdrops promoting new projects. Scammers, under the guise of free token distributions, may request your private key or wallet connection to a fake site, giving them full access to your funds.
The best way to secure your assets is to ignore tokens that appear in your wallet without your involvement and only use verified platforms for transactions.
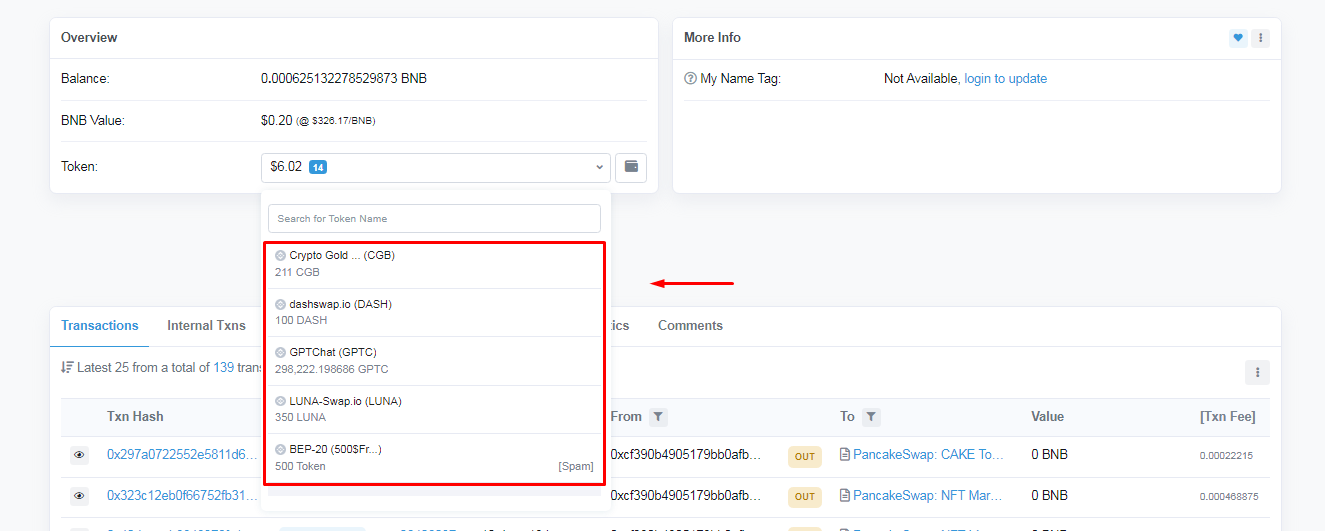
A New Wallet Appears on a Marketplace
When a new wallet is introduced or you are required to interact with an unfamiliar site that demands wallet connection, exercise caution. Do not rush to download a new wallet or import your seed phrase into it—this could lead to the loss of all your assets.
Only trust wallets downloaded from the official websites of projects. If you interact with an unverified site, never use a wallet containing your primary assets or input your seed phrase. Instead, create a new wallet with a minimal balance specifically for such purposes, especially when working with testnets or other experimental activities.
For maximum security, create separate wallets for different tasks: holding, trading, participating in airdrops, testnets, farming, and other activities. This approach helps divide risks and prevent the loss of all assets in case one wallet is compromised. While this requires time and attention, it significantly enhances the safety of your funds.
Fake Startups
Fake startups are a sophisticated scam. At first glance, the project seems reliable: active social media, contests, token presales, and whitelist participation. However, at the final stage, users are invited to purchase tokens before listing. Once the price rises, the token becomes unsellable, or the liquidity pool is emptied, and the project disappears with the funds.
Such schemes are difficult to detect in advance, especially if the scam is disguised as a successful project. Remember: scams can happen even with well-known projects. Never invest all your funds in one project, and always be prepared for the unexpected.
Scams Involving Crypto Purchases via P2P Exchanges
Scammers may offer to sell Bitcoin below market price, claiming they need to build a reputation. They insist on using the Exodus wallet, claiming to be "official partners." After installation and a restart of the wallet, the user sees BTC credited to their balance, but it’s an illusion—the transaction is not confirmed on the blockchain. The scammers then urge the user to quickly send USDT, and once the funds are transferred, the Bitcoin disappears because the transaction was canceled.
How to Protect Yourself:
- Always check the transaction hash.
- Wait for confirmations before proceeding.
- Use only trusted P2P exchanges.





